



8.1. Introduction to Computer Networks [src]
A computer network, often simply referred to as a network, is a collection of computers and devices interconnected by communications channels that facilitate communication and allows sharing of resources and information among interconnected devices.
Networks may be classified according to a wide variety of characteristics such as the medium used to transport the data, communications protocol used, scale, topology, organizational scope, etc. The Internet module introduced most of these classifications.
The medium used could be copper wire, fiber optics, radio, microwave, laser, etc. We will focus on two generic types: wired (connected by a palpable, visible medium) and wireless (connected by radio). Note that in all cases, the network devices (or nodes) are connected by electromagnetic radiation – the signal. The underlying difference between wired and wireless, is that in wired applications the signal is channeled through a physical medium, that guides and protects it. Whereas wireless requires that the signal be broadcast. This difference means that, in general, nodes connected by wired media can be further from one another, and are more secure & private.
A communications protocol defines the formats and rules for exchanging information via a network. Well-known networking protocols are Ethernet, which is a family of protocols used in local area networks, and the Internet Protocol suite (IP), which is today nearly ubiquitous in any computer network, including the Internet.
The scale (size) and organizational scope of the network leads to classifications such as:
- PAN – personal area networks: used by individuals and managed by the individual (or their corporate IT department). Closely related to an individual's Body Area Network.
- LAN – local area networks: encompassing a room, building or campus and managed by the organization that owns the property
- HAN – home area networks: LANs that encompass a person's domicile and surrounding environs, managed by a (typically) non-IT family member
- MAN – metropolitan area networks: encompassing a city; usually managed as a "public service" by a corporate entity
- WAN – wide area networks: a regional or national network, typically managed by a corporation
You might care to note that most of these are talking about a single, cohesive, well-defined network, often run by a single corporation. Conecting any one to another creates an internet (short for internetwork). The biggie of course is the Internet – distinguished by a captial I – which connects a huge number of networks world-wide. The distinction is sometimes pedantic, as our "campus network" – closest to a MAN – actual connects several smaller networks.
- GAN – global area network: a network used for supporting mobile communications across an arbitrary number of wireless LANs, satellite coverage areas, mobile phone networks, etc. The key challenge in mobile communications is handing off the user communications from one local coverage area to the next.
Computer networks are the core of modern communication. All modern aspects of the Public Switched Telephone Network (PSTN) are computer-controlled, and telephony increasingly runs over the Internet Protocol, although not necessarily the public Internet. The scope of communication has increased significantly in the past decade, and this boom in communication would not have been possible without the progressively advancing computer network. Computer networks, and the technologies needed to connect and communicate through and between them, continue to drive the computer hardware, software, and peripheral industries. This expansion is mirrored by growth in the numbers and types of users of networks, from the researcher to the home user.

Personal Area Network - Internet
By Paul Mullins: constructed
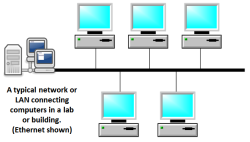
Local Area Network - Internet
By Paul Mullins: constructed
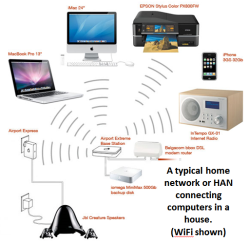
Home Area Network - Internet
By Paul Mullins: constructed

Metropolitan Area Network - Internet
By Paul Mullins: constructed
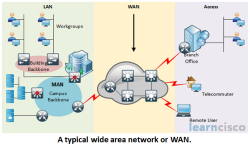
Wide Area Network - Internet
By Paul Mullins: constructed

Global Area Network - Internet
By Paul Mullins: constructed
Computer network properties
Networks facilitate communications. Using a network, people can communicate efficiently and easily via email, instant messaging, chat rooms, telephone, video telephone calls, and video conferencing.
Networks permit sharing of files, data, and other types of information. In a network environment, authorized users may access data and information stored on other computers on the network. The capability of providing access to data and information on shared storage devices is an important feature of many networks.
Networks share network and computing resources. In a networked environment, each computer on a network may access and use resources provided by devices on the network, such as printing a document on a shared network printer and using a file or web server. Distributed computing uses computing resources across a network to accomplish tasks.
Networks may be insecure. Network traffic might be intercepted. A computer network may be used by computer hackers to deploy computer viruses or computer worms on devices connected to the network, or to prevent these devices from normally accessing the network (denial of service).
Networks may interfere with other technologies. Power line communication strongly disturbs certain forms of radio communication, e.g., amateur radio. It may also interfere with "last mile" access technologies such as DSL.
A complex computer network may be difficult to set up. It may also be very costly to set up an effective, safe computer network in a large organization or company.
Connection Medium
Wired technologies
Twisted pair wire is the most widely used medium for (wired) telecommunication. Twisted-pair cabling consists insulated copper wires that are twisted into a helix (see image to the right). Ordinary telephone wires consist of one pair of wires. Computer networking cabling (wired Ethernet as defined by IEEE 802.3) consists of 4 pairs of copper cabling that can be utilized for both voice and data transmission. The use of two wires twisted together helps to reduce interference (crosstalk and electromagnetic induction). The transmission speed ranges from 2 Mbps (million bits per second) to 10 Gbps (billion bits per second). Twisted pair cabling comes in two forms which are Unshielded Twisted Pair (UTP) and Shielded twisted-pair (STP) which are rated in categories (CAT8, CAT7, CAT6, CAT5,...) which are manufactured in different increments for various scenarios. CAT 5 UTP is common at present.

Category 6 Twisted Pair
By Agott (Own work) [CC-BY-SA-3.0], via Wikimedia Commons

Typical UTP connection
By David J. Fred (Dfred) (Own work) [CC-BY-SA-2.5], via Wikimedia Commons
Recall that network data transfer rates are generally stated in bits per second, not bytes per second. Hence, an 8 Mbps connection will support downloads at (up to) 1 MBps, or a 4 MB photo will take at least 4 seconds to download.
Coaxial cable is widely used for cable television systems and local area networks in homes, office buildings, and other work-sites. The cables consist of a, relatively large, copper or aluminum wire wrapped with an insulating layer, all of which are surrounded by a conductive layer (shield). The layers of insulation & shielding help minimize interference and distortion. Transmission speed ranges from 200 Mbps to more than 500 Mbps.

Coaxial cable
By Tkgd2007 (Own work) [CC-BY-3.0], via Wikimedia Commons

BNC coax connector
Meggar [GFDL or CC-BY-SA-3.0], via Wikimedia Commons
Optical fiber cable consists of one or more filaments of glass fiber wrapped in protective layers that carries data by means of pulses of light, which can travel over extended distances. Fiber-optic cables are not affected by electromagnetic radiation. (Interference from electromagnetic radiation, as from the elevator located next to your office, is one of the key reason for all the "shielding" talked about above. Signals escaping from the medium, which can be "tapped," are another reason.)
Transmission speed of fiber optics may reach trillions of bits per second (Tbit/s). The transmission speed is hundreds of times faster than for coaxial cables and thousands of times faster than a twisted-pair wire. The capacity may be further increased by the use of colored light, i.e., light of multiple wavelengths. Instead of carrying one message in a stream of monochromatic light impulses, this technology can carry multiple signals simultaneously in a single fiber.

A TOSLINK fiber optic cable with a clear jacket that has a laser being shone onto one end of the cable. The laser is being shone into the left connector; the light coming out the right connector is from the same laser.
By Hustvedt (Template:One) [CC-BY-SA-3.0 or GFDL], via Wikimedia Commons
Wireless technologies
Terrestrial microwave uses Earth-based transmitters and receivers. The equipment looks similar to satellite dishes. Terrestrial microwaves are limited to line-of-sight (due to the frequency range used), requiring long paths to include relays. The distance between relay stations is spaced approximately, 48 km (30 miles) apart. Microwave antennas are usually placed on top of buildings, towers, hills, and mountain peaks.

Microwave relay station
By Vladimir Menkov (Own work (Own photo)) [GFDL, CC-BY-SA-3.0 or CC-BY-SA-2.5-2.0-1.0], via Wikimedia Commons
Communications satellites also use microwave radio as their telecommunications medium (because microwaves are not deflected by the Earth's atmosphere). Geosynchronous satellites are stationed in space, typically 35,400 km (22,200 miles) above the equator. These Earth-orbiting systems are capable of receiving and relaying voice, data, and TV signals. The distance causes significant latency (delay) in the signal – typically 1-1.5 seconds round trip time. Satellites in low-earth orbit, such as the constellations of Globalstar and Iridium, have significantly lower delays (~40 msec) and require less power, but the coverage area of a single satellite is greatly reduced, requiring a constellation (net) of cooperating satellites.

WildBlue satellite Internet dish on the side of a house
CC BY-SA 3.0, Link
Cellular and Personal Communications Service systems use several radio communications technologies. The systems are divided into different geographic areas, called cells. Each area has a low-power transmitter or radio relay antenna device to relay calls from and to a base station. The base station handles hand off from one cell to another (when you are driving, e.g.) and connecting through a gateway to the Internet. Calls are relayed to the public switched telephone network (PSTN) through a mobile switching center (MSC). Typically, the only part of the system that is wireless is the connection between the PCS device and the local tower.
Note that, to accomplish the "hand off", your cell phone is in fairly constant communication with local cell towers even when you are not using it. (That's how they locate a cell phone in all those TV shows, with "triangulation" and GPS both providing a finer location.)
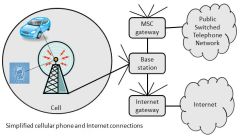
Simplified Cellular Internet
By Paul Mullins: constructed
Wireless local area networks use a high-frequency radio technology, similar to digital cellular, and a low-frequency radio technology. Wireless LANs use "spread spectrum" technology to enable communication between multiple devices in a limited area. Wireless devices, such as a laptop computer, need a wireless transceiver to connect to a wireless access point (router or bridge) which is in turn connected to a LAN. The LAN is typically connected through a router to the Internet. In home networks, the wired LAN and wireless router are often the same device.

Laptop & wireless access point
Photo taken by Clawed. Licensed under the Creative Commons Attribution ShareAlike 3.0 License
Infrared light communication (without a fiber) can transmit signals between devices within small distances of, typically, no more than 10 meters. In most cases, line-of-sight propagation is used, which limits the physical positioning of communicating devices.
Bluetooth is a proprietary open wireless technology standard for exchanging data over short distances (using short wavelength radio transmissions) from fixed and mobile devices, creating personal area networks (PANs) with high levels of security.[src]
Near Field Communication employs electromagnetic induction between two loop antennas when NFC devices are within 4 cm (1.57 in) of each other. NFC devices are used in contactless payment systems, similar to those used in credit cards and electronic ticket smartcards. NFC is used for social networking, for sharing contacts, photos, videos or files. NFC-enabled devices can act as electronic identity documents and keycards.[src]
Basic hardware components
Apart from the physical communications media themselves, networks include additional basic hardware building blocks interconnecting their nodes, such as network interface cards (NICs), hubs, bridges, switches, and routers. How these devices work is often stated in terms of the layered OSI model of communications in networks which provides both a way to think about the complex interactions in a computer network and a structured way to implement hardware and software.
Consider the cellular communication described above. Clearly, sending and receiving calls is a complicated bit of technology. At the lowest level, it involves radio communication between the phone and the tower (antenna) and wired communication between other system components. A call to a person right next to you is routed by the base station back to the same antenna, and then to their phone. Mostly, we don't want to have to worry about that. Users are interested in only the top layer — a number is dialed (or text sent to a friend) and communication seems to occur directly from phone to phone. We don't worry about how (except, perhaps, when things aren't working as expected).
The OSI model allows device manufacturers and software developers to do the same thing. At the top level (or layer), we pretend we are communicating directly with another device at the top layer. At layer 3, we pretend we are talking directly to another device at layer 3. The lower-level details are always left to someone else — all the way down to the actual physical connection, where the engineers have to make it happen.
Layered communication model
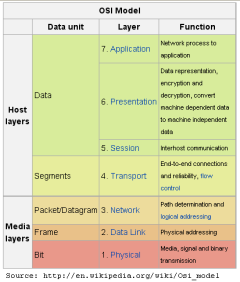
OSI layers
By Paul Mullins: screenshot of CCSA text
A layer 3 "device" communicates directly (conceptually) with other layer 3 "devices". It does not have to worry about layer 2 or layer 1.
Similarly, a layer 2 "device" does not concern itself with layer 1.
Network interface cards
A network card, network adapter, or NIC (network interface card) is a piece of computer hardware designed to allow computers to physically access a networking medium. It provides a low-level addressing system through the use of MAC addresses. Each Ethernet network interface has a unique MAC address which is usually stored in a small memory device on the card, allowing any device to connect to the network without creating an address conflict.

100MBit Ethernet NIC PCI card
By afrank99 (Own work) [CC-BY-SA-2.0], via Wikimedia Commons
Repeaters and hubs
A repeater is an electronic device that receives a signal, cleans it of unnecessary noise, regenerates it, and retransmits it at a higher power level. This allows the signal to cover longer distances without degradation, or to the other side of an obstruction. In most twisted pair Ethernet configurations, repeaters are required for cable that runs longer than 100 meters. A repeater with multiple ports is known as a hub. Signals are repeated to all ports.
Repeaters work on the Physical Layer (layer 1) of the OSI model. Repeaters require a small amount of time to regenerate the signal. This can cause a propagation delay which can affect network communication when there are several repeaters in a row. Because of this, many network architectures limit the number of repeaters that can be used.
Today, repeaters and hubs have been made mostly obsolete by switches (see below).
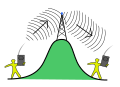
Wireless repeater concept – public domain image

Four port edimax hub – public domain image
Bridges
A network bridge connects multiple network segments at the data link layer (layer 2) of the OSI model. Bridges initially broadcast to all ports. However, bridges do not simply copy traffic to all ports, as hubs do, but learn which MAC addresses are reachable through specific ports. Once the bridge associates a port and an address, it will send traffic for that address to that port only. This reduces unnecessary traffic and makes "spying" more difficult.
Bridges learn the association of ports and addresses by examining the source address of frames that it sees on various ports. Once a frame arrives through a port, its source address is stored and the bridge assumes that MAC address is associated with that port. The first time that a previously unknown destination address is seen, the bridge will forward the frame to all ports other than the one on which the frame arrived.
Bridge passing allowed traffic only from LAN to LAN – public domain image
Switches
A network switch is a device that forwards and filters OSI layer 2 datagrams (chunks of data communication) between ports (connected cables) based on the MAC addresses in the packets. A switch is distinct from a hub in that connected devices can't interfere with (or talk over) one another. A switch normally has numerous ports, facilitating a star topology for devices that do not share their connection.
Switches make forwarding decisions of frames on the basis of MAC addresses (like a bridge). When possible, it only forwards the frames to the ports involved in the communication rather than all ports connected.
The term switch is used loosely in marketing to encompass devices including routers and bridges, as well as devices that may distribute traffic based on load or by application content (e.g., a Web URL identifier).
A small office network may use one or more switches. Your home network is unlikely to. Most home networks have a router (below) which incorporates a hub and may use a (wireless) bridge.

Star topology for a switch
By Umapathy (Own work) [CC-BY-SA-3.0 or GFDL], via Wikimedia Commons
3Com rack mounted switch. Connects up to 24 devices which may include one or more additional switches.
public domain image
Routers
A router is an internetworking device that forwards packets between networks by processing information found in the datagram or packet (Internet protocol information from Layer 3 of the OSI Model). In many situations, this information is processed in conjunction with the routing table (also known as forwarding table). Routers use routing tables to determine what interface (network connection) to forward packets to.
A car navigation device provides a complete route (map) from current location to destination. A network router makes the decision of which way to send data when it arrives (at an intersection), thus choosing only the next step in the overall route taken by the data. This allows the network to adapt to current conditions. (Quite similar to a navigation device that might decide to change the route selected at any intersection based upon current traffic conditions.)
A "circuit" can be formed by making sure the router always chooses the same interface for certain traffic. (Like a parade route.)

Linksys Wireless router – public domain image
Routers connecting LANs – public domain image
Firewalls
A firewall (as discussed earlier) is important to network security. It typically rejects access requests from unsafe sources while allowing actions from recognized ones. A firewall can be a stand-alone device, but a typical PC and home wireless router both include firewall software.
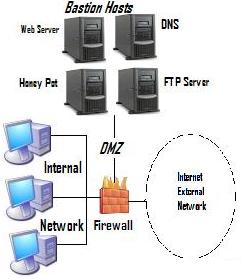
Internet firewall concept – public domain image







