
Radio Frequency IDentifier tags are becoming commonplace. They are in many credit cards and soon may be in most of products you buy. At SRU, they are called "contactless tokens" and used on campus to purchase many items.
A reader, a device used by the merchant, or whoever is scanning the tag, sends out a query from a relatively powerful antenna. Nearby tags all receive the query (assuming it is at the correct radio frequency). Simple tags, like those used for clothing, are not encrypted and respond by broadcasting whatever information is stored – usually a product identifier. If the tag is encrypted, it may also simply respond, usually sending some information "in the clear" and some encrypted. A well-designed encrypted tag expects to receive a password (key). It matches that key to its stored key, before responding. In any case, the response is received by the reader, decrypted if necessary, and passed to a computer for processing.
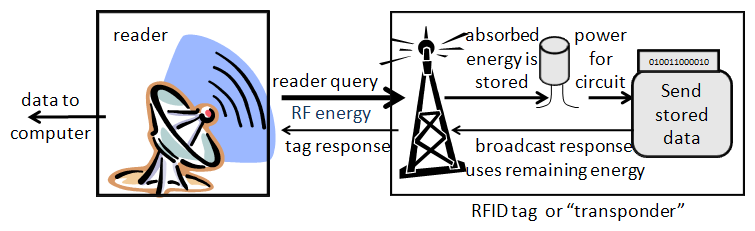
The cheapest tags have no power source. They use the energy absorbed from the reader's transmission to broadcast back their data, usually a product identifier. This is similar to the way an echo works. Your shout, in a canyon, travels outward until it hits a surface like the canyon wall. Part of the sound is reflected back to you as an echo. Obviously, what you hear is greatly diminished, as much of the energy is lost. The reflected sound is also modified somewhat by the shape of the reflecting surface.
RFID tags work similarly. They have a small antenna that "hears" the radio broadcast (query) from the reader. The energy of the signal received is enough to power the small amount of circuitry involved in sending back its data – an echo that is (significantly) modified.
The range at which these devices work are typically stated for a particular use. In a store, for example, the system would not work if all the tags within 10 meters responded when a customer was trying to check out. Systems can be designed to read only a few inches from the reader. This proximity depends on both the tag and the reader, however. Misuse of the tags, as privacy advocates claim will occur, can not be expected to follow the rules. The "bad guys" will use as large an antenna and as powerful a reader as possible to spy on the signal transmitted (or, even to change data on the tag).
Privacy advocates have raised many concerns regarding RFID (see www.privacy.org). One concern I have not seen elsewhere involves tracking.
Suppose, each piece of clothing you wear – shoes to underwear – has a product tag. They don't identify you, of course. You also have some in your wallet that do identify you, but they are encrypted. (Encryption per se does not affect this scenario, as you don't have to be able to understand the data received. However, if proper security techniques are used, the tag will only respond if a secret key is known.) Your wallet does have a tag, as do most other items you may be carrying. Let say there are only eight tags.
Those eight tags in combination make it easy for someone to track you electronically, perhaps from a nearby van. They become a fairly detailed description: the guy with Levi jeans, Izod polo shirt, Adidas shoes, etc. Especially detailed, if the tags carry unique identifiers (serial numbers).
As I see it: Product tags are of no use to the consumer. They should be removable or allow disabling upon purchase.
