


6b.5. Privacy
Privacy does not mean cutting yourself off from the world. You don't have to walk around wearing a mask, drive an anonymous car, and pay for everything with cash. Privacy means being able close the window curtains and lock your door when you wish, allowing those you trust into whatever parts of your life you choose to let them into, while knowing that your actions in public are just that – public actions.
If you choose to share pictures with the world on Facebook, you can. However, you should be able to send an email (text or photo) to your lover with a reasonable expectation that the content will remain private — at least to the degree that the person you are sending it to cooperates.
Some have claimed that privacy doesn't exist anymore. Certainly, the Internet has given new meaning to the phrase "public actions". In the U.S., much depends on whether your had a reasonable expectation of privacy.

Blinds open, drawn & partially drawn. Door locked?
Betty Longbottom [CC-BY-SA-2.0], via Wikimedia Commons

Gossips in the Altstadt in Sindelfingen, Germany
By Rebecca Kennison (Own work) [GFDL, CC-BY-SA-3.0 or CC-BY-2.5], via Wikimedia Commons
A purchase in your local pharmacy once was a public action viewable solely by the pharmacist and/or clerk, and anyone who happened to be standing nearby. Ethics, etiquette, social norms and the speed of gossip limited who might learn of your purchase. Ethics, etiquette and social norms vary among people and societies. They may be unrecognizably different for businesses and some small percentage of people. Unfortunately, with the vast number of people on the Internet, even a small percentage is a very large number. And, the speed at which gossip can travel is now enormous.
Free instant messenger gossip
By Mikael Halendal (http://developer.imendio.com/projects/gossip/)[see page for license], via Wikimedia Commons
Gossip is good and useful?
Privacy [src]
Information privacy (like your medical records) is related to our discussion, but we will focus on the Internet.
Internet privacy involves the desire or mandate of personal privacy concerning transactions or transmission of data via the Internet. It also involves the exercise of control over the type and amount of information revealed about a person on the Internet and who may access said information.
Privacy International 2007 privacy ranking
By Wüstling [GFDL or CC-BY-SA-3.0-2.5-2.0-1.0], via Wikimedia Commons
Anonymity [src1] [src2]
People with only a casual concern for Internet privacy may achieve an adequate level of privacy through controlled disclosure of personal information. The revelation of IP addresses, non-personally-identifiable profiling, and similar information might become acceptable trade-offs for the convenience that users could otherwise lose using the workarounds needed to suppress such details rigorously. On the other hand, some people desire much stronger privacy. In that case, they may try to achieve Internet anonymity – use of the Internet without giving any third parties the ability to link the Internet activities to personally-identifiable information of the Internet user.

Theater mask
By Deror avi (Own work) [Attribution, CC-BY-SA-3.0 or GFDL], via Wikimedia Commons
Most commentary on the Internet is essentially done anonymously, using unidentifiable pseudonyms. While these names can take on an identity of their own, they are frequently separated from and anonymous from the actual author, and, according to the University of Stockholm, creating more freedom of expression, and less accountability. For example, the online encyclopedia Wikipedia is collaboratively written mostly by authors using either unidentifiable pseudonyms or IP address identifiers, although a few have used identified pseudonyms or their real names.
Full anonymity on the Internet, however, is not guaranteed since IP addresses, in principle, can be tracked, allowing someone to identify the computer from which a certain post was made, albeit not the actual user. Free anonymizing services such as I2P - The Anonymous Network or Tor address the issue of IP tracking. Their distributed technology approach may grant a higher degree of security than centralized anonymizing services where a central point exists that could disclose one's identity. Ixquick, the (self proclaimed) "world's most private search engine", does not record IP addresses.
Sites such as Chatroulette and Omegle capitalize on the current fascination with anonymity. They are examples of anonymous chat or stranger chat.

Invisible Internet Project
By I2P Team (Own work (Screenshot))[see page for license], via Wikimedia Commons
In order to keep information private, people need to be careful of what they submit and look at online. Filling out forms and buying merchandise on-line may constitute a public transaction and it is certainly a release of the information to another party. That information becomes tracked and potentially sold to third parties. Companies are hired not only to watch what you visit online, but to analyze the information and send advertising based on your browsing history. (Note that this is not "spying". In the absence of malware, these actions are taken cooperatively by the web site and the third parties. Use of HTTPS will not prevent this.)
Social Networking [src]
Social networking sites are in some ways intended to broadcast or share personal information. Privacy measures are provided on several social networking sites to try to provide their users with protection for their personal information. On Facebook for example privacy settings are available for all registered users. The settings available on Facebook include the ability to block certain individuals from seeing your profile, the ability to choose your "friends," and the ability to limit who has access to your pictures and videos. Privacy settings are also available on other social networking sites such as E-harmony, Google+ and MySpace. A primary complaint is that the default settings favor openness, not privacy. It is the user's responsibility to apply such settings when providing personal information on the Internet.

Social networking
By Paul Mullins: constructed
Prior to the social networking site explosion over the past decade, there were early forms of social network technologies that included online multiplayer games, blog sites, news groups, mailings lists and dating services. These all created a backbone for the new modern sites, and, even from the start of these older versions, privacy was an issue (with complaints of stalking, harassment, etc.).
Social networking sites have become very popular within the last decade. With the creation of Facebook, Google+, Twitter, Instagram, etc., many people are giving their personal information out on the internet. These social networks keep track of all interactions used on their sites and save them for later use. Most users are not aware that they can modify the privacy settings and that unless they modify them, their information is open to the public. On Facebook privacy settings can be accessed via the drop down menu under account in the top right corner. There, users can change who can view their profile and what information can be displayed on their profile. In most cases, profiles are open to either "all my network and friends" or "all of my friends." Also, information that shows on a user's profile such as birthday, religious views, and relationship status can be removed via the privacy settings. If a user is under 13 years old they are not able to make a Facebook or a MySpace account, however, this is not regulated.

Online social networking sites
public domain image
Another privacy issue with social networks is the privacy agreement. Typically, the privacy agreement states that the social network owns all of the content that users upload. This includes pictures, videos, and messages. All are stored in the social networks database, even if the user decides to terminate his or her account. Additionally, the advent of the Web 2.0, which is the system that facilitates participatory information sharing and collaboration on the World Wide Web, allows for Facebook and other social networking media web sites filter through the advertisements, assigning specific ones to specific age groups, gender groups, and even ethnicities. Web 2.0 has caused social profiling and is a growing concern for Internet privacy. (Targeted advertising based on your "likes" are less controversial.)
A non-legal-advice opinion
Facebook claiming rights to anything you post is a persistent interpretation of their privacy policy. I don't see it, but then, I'm not a lawyer.
It does say that if you release information (photos) to third party apps, you're subject to their policies. The problem seems to be that users do not understand that those apps are not "Facebook apps". They are apps written by others to use on Facebook. New company, new rules. Research it before you use the app.
The Facebook Statement of Rights & Responsibilities clearly says that while intellectual property (IP) is (actively) on Facebook, they can use it – for pretty much anything they want. But, you retain ownership. When you delete the photo or other IP content, they lose the right to use it.
It also says that if you have shared information with other members, third party apps, or the world, that they (obviously) can do what they want with your data – subject to any agreements made with them.
Consider adding a watermark copyright notice to photos (IP), set privacy settings appropriately, choose friends carefully, use apps that provide a policy you agree with, and only post what you are willing to share with those people... forever. (See previous sidebar on memory of the Internet.)
Social networking has redefined the role of Internet privacy. Since users are willingly disclosing personal information online, the role of privacy and security is somewhat blurry. Sites such as Facebook, Myspace, and Twitter have grown popular by broadcasting status updates featuring personal information such as location. Facebook "Places", in particular, is a Facebook service which publicizes user location information to the networking community. Users are allowed to "check-in" at various locations including retail stores, convenience stores, and restaurants. Also, users are able to create their own "place", disclosing personal information onto the Internet. This form of location tracking is automated and must be turned off manually.

Concept of Google Latitude and Facebook Places
By Paul Mullins: constructed
Computer users, who save time and money, and who gain conveniences and entertainment, may or may not have surrendered the right to privacy in exchange for using a number of technologies including the Web. For example: more than a half billion people worldwide have used a social network service, and of Americans who grew up with the Web, half created an online profile and are part of a generational shift that could be changing norms. The social network Facebook progressed from U.S. college students to a 70% non-U.S. audience, but in 2009 estimated that only 20% of its members use privacy settings.

#223: Facebook Privacy & Security
Who is your ISP?
There's really no telling who you or your parents selected for your home (see some options below). But, many of you have a smartphone. Your service provider is also an ISP. And, while on campus, the University is your ISP. At work, your employer is. Your employer and university might contract out the actual ISP (connecting to the Internet) part, but you are using their facilities also.
In the US, this generally means that your employer and/or university can monitor your online activity – not to put too fine a point on it – but actually all of your activity on their computers and their network (or phone). Ask to see an "acceptable use policy" or AUP. If asked to sign one, read it first.
You may not be concerned with workplace privacy and online privacy yet, but you should be. I recommend perusing the:
- Electronic Privacy Information Center
- Electronic Frontier Foundation, and
- Computer Professionals for Social Responsibility
We will talk about ISPs in module 8.
Internet Service Providers [src]
Internet users obtain Internet access through an Internet service provider (ISP). All data transmitted to and from users must pass through the ISP. Thus, an ISP has the potential to observe users' activities on the Internet.
However, ISPs are usually prevented from participating in such activities by law, as well as ethical and business reasons. (At SRU, the University acts as your ISP, although without a direct business relationship.)
Despite these legal and ethical restrictions, some ISPs, such as British Telecom (BT), are planning to use deep packet inspection technology provided by companies such as Phorm in order to examine the contents of the pages that people visit. By doing so, they can build up a profile of a person's web surfing habits, which can then be sold on to advertisers in order to provide targeted advertising. BT's attempt at doing this will be marketed under the name 'Webwise'.
Normally ISPs do collect at least some information about the consumers using their services. From a privacy standpoint, ISPs would ideally collect only as much information as they require in order to provide Internet connectivity (IP address, billing information if applicable, etc).
Which information an ISP collects, what it does with that information, and whether it informs its consumers, pose significant privacy issues. Beyond the usage of collected information typical of third parties, ISPs sometimes state that they will make their information available to government authorities upon request. In the US and other countries, such a request does not necessarily require a warrant.
An ISP cannot know the contents of properly-encrypted data passing between its consumers and the Internet. For encrypting web traffic, https has become the most popular and best-supported standard. Even if users encrypt the data, the ISP still knows the IP addresses of the sender and of the recipient.
An Anonymizer such as I2P - The Anonymous Network or Tor can be used for accessing web services without them knowing your IP address and without your ISP knowing what the services are that you access.
Photographs [src]
Today many people have digital cameras and post their photos online. The people depicted in these photos might not want to have them appear on the Internet.
The Harvard Law Review published a short piece called "In The Face of Danger: Facial Recognition and Privacy Law", much of it explaining how "privacy law, in its current form, is of no help to those unwillingly tagged." Any individual can be unwillingly tagged in a photo and displayed in a manner that might violate them personally in some way, and by the time Facebook gets to taking down the photo, many people will have already had the chance to view, share, or distribute it. Furthermore, traditional tort law does not protect people who are captured by a photograph in public because this is not counted as an invasion of privacy.
Profile, and other posted, pictures can allow people to invade a person's privacy by finding out information that can be used to track and locate a certain individual. In an article (Celebrities' Photos, Videos May Reveal Location) featured in ABC news, it was stated that two teams of scientists found out that Hollywood stars could be giving up information about their private whereabouts very easily through pictures uploaded to the Internet. Moreover, it was found that pictures taken by smartphones automatically attach the latitude and longitude of the picture taken through metadata unless this function is manually disabled.
EXIF Data
The exif data, stored automatically with your pictures by some cameras, includes camera settings, date, etc. But, it also includes (in many cases) the GPS location at which the picture was taken. This is not good if you are hiding out from an abusive spouse and just want to show everyone on Facebook that the kids are okay. Or, eagles are nesting in your backyard – prepare for a parade of people, including PETA and the government.
So, you're sensitive to your friend's desire to not appear on Facebook and you blocked out her face with a photo editor — exif also contains a thumbnail, usually of the original photo.
Exif data can be removed or changed without affecting the image using a photo editing tool, such as (the free) IrfanView.
The web is "stateless"
An HTTP (web) server treats each interaction as a separate, independent request. So, how does Amazon know what's in your shopping cart? Why don't you have to login on Facebook with each request? Cookies! A session cookie, originally sent by the server, is returned with each transaction to remind the server who you are.

Cookie sent back with each page request
By Tizio (Own work) [GFDL or CC-BY-SA-3.0], via Wikimedia Commons
Cookies [src]
An HTTP cookie is data stored on a user's computer that assists in automated access to web sites or web features, or other state information required in complex web sites. It may also be used for user-tracking by storing special usage history data in a cookie. Cookies are a common concern in the field of privacy. As a result, some types of cookies are classified as a tracking cookie. Although web site developers most commonly use cookies for legitimate technical purposes, cases of abuse occur. In 2009, two researchers noted that social networking profiles could be connected to cookies, allowing the social networking profile to be connected to browsing habits.
Systems do not generally make the user explicitly aware of the storing of a cookie. Although some users object to that, it does not explicitly relate to Internet privacy. It does however have implications for computer privacy, and specifically for computer forensics.

For a complete discussion on cookies check out the article by InfoSec. It includes how it works and the "risks associated with cookies".
The original developers of cookies intended that only the web site that originally distributed cookies to users could retrieve them, therefore returning only data already possessed by the web site. However, many web pages use images loaded from some other web site. (Most of the images used in these notes are loaded directly from commons.wikimedia.org.)When that other web site stores a cookie, it is called a third-party cookie. Possible consequences include:
- the placing of a personally-identifiable tag in a browser to facilitate web profiling, or,
- use of cross-site scripting or other techniques to steal information from a user's cookies.
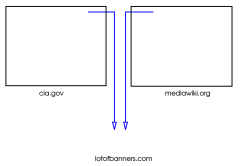
In this fictional example, an advertising company has placed banners in two Web sites. Hosting the banner images on its servers and using third-party cookies, the advertising company is able to track the browsing of users across these two sites.[src]
By Tizio [GFDL or CC-BY-SA-3.0], via Wikimedia Commons
The image above does not exist on the SRU web servers, it is loaded directly from commons.wikimedia.org – but they aren't tracking you!
Some users choose to disable cookies in their web browsers - as of 2000 a Pew survey estimated that proportion of users at 4%. Such an action eliminates the potential privacy risks, but may severely limit or prevent the functionality of many web sites. All significant web browsers have this disabling ability built-in, with no external program required. As an alternative, users may frequently delete any stored cookies. Some browsers (such as Mozilla Firefox, Opera and Dolphin) offer the option to clear cookies automatically whenever the user closes the browser. More recently, every major browser provides a "private" mode that (typically) deletes all local history of the browsing session when you finish. Make sure you check out how it works on your browser!
The process of profiling (also known as "tracking") assembles and analyzes several events, each attributable to a single originating entity, in order to gain information (especially patterns of activity) relating to the originating entity. Some organizations engage in the profiling of people's web browsing, collecting the URLs of sites visited. The resulting profiles can potentially link with information that personally identifies the individual who did the browsing.
Some web-oriented marketing-research organizations may use this practice legitimately, for example: in order to construct profiles of 'typical Internet users'. Such profiles, which describe average trends of large groups of Internet users rather than of actual individuals, can then prove useful for market analysis. Although the aggregate data does not constitute a privacy violation, some people believe that the initial profiling does.
Profiling becomes a more contentious privacy issue when data-matching associates the profile of an individual with personally-identifiable information of the individual.
HotSpots
In Fall 2010, a FireFox (browser) add-on called FireSheep was released. FireSheep scans a HotSpot for other users logged into Facebook or Twitter. When found, they appear (profile photo and name) in a sidebar of the attacker's browser. The attacker need only double-click the icon to hijack the session. Faceniff is an Android app that acts similarly.
Lots of (prospective) employers now research (prospective) employees on social networking sites. Imagine the damage that even a practical joke could cause!
In Jan 2011, Facebook enabled https-only browsing. Twitter followed suit in March 2011. In both cases, you must turn it on!

#96 HotSpot Safety
Cookie theft and session hijacking [src]
Most web sites use cookies as the only identifiers for user sessions, because other methods of identifying web users have limitations and vulnerabilities. If a web site uses cookies as session identifiers, attackers can impersonate users' requests by stealing a full set of victims' cookies. From the web server's point of view, a request from an attacker has the same authentication as the victim's requests; thus the request is performed on behalf of the victim's session.
In this scenario someone listens to other's transactions on a broadcast network and steals their authentication cookies, allowing the attacker to "become you". This is most obviously a problem on any open wireless network, but includes encrypted Wi-Fi networks where others have the password (as in most hotspots).
The solution: don't use wireless networks for secure transactions and, if you do, only do so with sites that use https throughout the session, not just for login. If a site you "need" to use doesn't provide this option, complain, loudly and often, until they do.
To be fair, network monitoring and session hijacking can occur on a wired network also. However, most wired networks today do not broadcast everything for everyone else to "hear", as is clearly done with wireless. And to hear anything on the wired network, the attacker has to first gain physical access to the network.
U.S. Laws [src]
- USA Patriot Act
- The purpose of this law, enacted on October 26, 2001 by former President Bush, was to enhance law enforcement investigatory tools, investigate online activity, as well as to discourage terrorist acts both within the United States and around the world. This act reduced restrictions for law enforcement to search various methods and tools of communication such as telephone, e-mail, personal records including medical and financial, as well as reducing restrictions for obtaining foreign intelligence.
- Electronic Communications Privacy Act (ECPA)
- This act makes it unlawful under certain conditions for an individual to reveal the information of electronic communication and contains a few exceptions. One clause allows the ISP to view private e-mail if the sender is suspected of attempting to damage the Internet system or attempting to harm another user. Another clause allows the ISP to reveal information from a message if the sender or recipient allows its disclosure. Finally, information containing personal information may also be revealed subject to a court order or law enforcement subpoena.
Privacy representatives from 60 countries have resolved to ask for laws to complement industry self-regulation, for education for children and other minors who use the Web, and for default protections for users of social networks. In the US, the Children's Online Privacy Protection Act applies to children under the age of 13.

#146 Protect your kids online
Privacy isn't just for you
This was written from the perpective of personal privacy. As we are about to switch to the topic of security, it makes sense to point out that both security and privacy can also have an impact on your professional life (and the lives of others). In the past, workers have had laptops stolen that contain confidential information, employees have used online forums to discuss patient health care, and corporate spying was, and is, common.
The more work overlaps with our personal lives, including simply using personal computers to access work, the more you have to be concerned about maintaining security and privacy of the information entrusted to you. You may have a legal, ethical and/or moral obligation to do so.







