


6b.6. Security [src1] [src2]
We have looked at malware, in an earlier module, as a class of software with malicious intent. We also looked at some of the system administration things you need to do to prevent infection and to reduce damages. Here, we look more closely at the primary source of the malware, the Internet, along with some additional threats.
Security & the Web
The Web has become criminals' preferred pathway for spreading malware. Cybercrime carried out on the Web can include identity theft, fraud, espionage and intelligence gathering. Web-based vulnerabilities now outnumber traditional computer security concerns, and as measured by Google, about one in ten web pages may contain malicious code. Most Web-based attacks take place on legitimate web sites, and most, as measured by Sophos, are hosted in the United States, China and Russia. The most common of all malware threats is SQL injection (database) attacks against web sites. The Web has been vulnerable to attacks like cross-site scripting that came with the introduction of JavaScript (a client-side, or browser, programming language) and were exacerbated to some degree by Web 2.0. Today, by one estimate, 70% of all web sites are open to cross-site scripting attacks on their users.
Proposed solutions vary to extremes. Large security vendors like McAfee already design governance and compliance suites – sort of a large anit-virus package for networks – to meet post-9/11 (US) regulations. Some, like Finjan, have recommended active real-time inspection of code and all content regardless of its source – like the on-access scan of an AV package, but for networks.
Some have argued that for an enterprise to see security as a business opportunity rather than simply a cost, ubiquitous, always-on digital rights management enforced in the infrastructure by a handful of organizations must replace the hundreds of companies that today secure data and networks. (Recall that companies use DRM to control access to information, not just to stop you from copying music.) While others believe that users sharing responsibility for computing safety is far preferable to locking down the Internet.
iPhone App Store control v. Android Marketplace freedom... parallels the argument about control over "code" on the Internet.
Should the WWW be the Wild, Wild West or controlled by a few benevolent powers (We'll Watch While you relax)?
Network layer security
The basic Internet protocol suite, TCP/IP, can be made secure with the help of cryptographic methods and protocols that have been developed for securing communications on the Internet. These protocols include HTTPS (technically, TLS) for web traffic , PGP for email, and IPsec for the network layer security.
Web site designers determine whether you can use HTTPS — you should refuse to use sites that ask for personal or financial information that are not using HTTPS, but why not use it everywhere, all the time? PGP mail currently requires user set up and is not used by most people. If PGP was standard on web-based mail services, like gmail, it might be in common use. Solutions at the network level, like IPsec, are invisible to the user and their applications. However, a key difference is that HTTPS and PGP provide protection from the desktop to the destination, while IPsec may only protect the data from gateway (router) to gateway (that is, between LANs, but not on the LAN).

Where host-host communication is secure. (IPsec can be implemented from host to host.)
By Paul Mullins: constructed
IPsec Protocol
This protocol is designed to protect communication in a secure manner using TCP/IP. It is a set of security extensions that provides security and authentication at the IP layer by using cryptography. The set of security services provided at the IP layer includes access control, data origin integrity, protection against replays, and confidentiality. The IPsec implementation can be in a host or gateway, giving protection to all IP traffic leaving the LAN.
Virtual private network [src]
A corporation may wish to keep its communications secure. They can then lease lines connecting all of the corporation sites, but roaming users, like a salesperson in a hotel, must still use the Public Switched Telephone Network (PSTN). Leased lines form an expensive private network; but the PSTN is not secure.
A virtual private network (VPN) is a computer network in which the links between nodes are carried by open connections or virtual circuits in some larger network (e.g., the Internet) instead of by physical wires. The lower level protocols of the virtual network are said to be tunneled through the larger network when this is the case. One common application is secure communications through the public Internet, whether IPsec or IP is used.
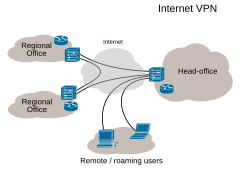
VPN: Each endpoint, including roaming users, has software to encrypt/decrypt data
By Ludovic.ferre (Virtual_Private_Network_overview.svg) [GFDL or CC-BY-SA-3.0-2.5-2.0-1.0], via Wikimedia Commons
 #253 Virtual private networks
#253 Virtual private networks
Electronic mail security (E-mail)
Pretty Good Privacy (PGP) provides confidentiality by encrypting messages to be transmitted or data files to be stored using a commercial-grade encryption algorithm. Email messages can be protected by using cryptography in various ways, such as the following:
- Signing an email message to ensure its integrity and confirm the identity of its sender.
- Encrypting the body of an email message to ensure its confidentiality.
- Encrypting the communications between mail servers to protect the confidentiality of both the message body and message header (to/from/subject/etc).
The first two methods, message signing and message body encryption, are often used together; however, encrypting the transmissions between mail servers is typically used only when two organizations want to protect emails regularly sent between each other. For example, the organizations could establish a virtual private network (VPN) to encrypt the communications between their mail servers over the Internet. Unlike methods that can only encrypt a message body, a VPN can encrypt entire messages, including email header information such as senders, recipients, and subjects. In some cases, organizations may need to protect header information. However, a VPN solution alone cannot provide a message signing mechanism, nor can it provide protection for email messages along the entire route from sender to recipient.
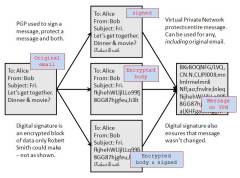
PGP protected and signed email, with VPN
By Paul Mullins: constructed
Secure/Multipurpose Internet Mail Extensions (S/MIME)
S/MIME provides a consistent means to securely send and receive MIME data (pictures, audio, or just about anything that is not plain text). S/MIME is not limited to email but can be used with any transport mechanism that carries MIME data, such Hypertext Transfer Protocol (HTTP).
Firewalls
A firewall is a device (hardware or software) designed to permit or deny network transmissions based upon a set of rules. It is frequently used to protect networks from unauthorized access while permitting legitimate communications to pass.
Most personal computer operating systems include software-based firewalls to protect against threats from the public Internet. Many routers that pass data between networks contain firewall components and, conversely, many firewalls can perform basic routing functions. Your PC is probably protected by a firewall on the PC itself and in the router you use to connect to the Internet.[src]
Role of firewalls in Internet security
Firewalls impose restrictions on incoming and outgoing packets to and from private networks. All the traffic, whether incoming or outgoing, must pass through the firewall; creating a checkpoint between the private network and the public Internet. At the checkpoint, network traffic can be analyzed to determine if it is allowed or should be filtered based on content or packet header (envelope) information. For example, firewalls can create a choke point based on a combination of the protocol used for the traffic, the source & destination host (IP address) and the application (TCP port number).
Firewalls can also serve as the platform for IPsec. Using "tunnel mode" capability, firewalls can be used to implement VPNs. Firewalls can also limit network exposure by hiding the internal network system and information from the public Internet.

A personal (PC) firewall
By Harald Mühlböck [FAL, GFDL or CC-BY-3.0], via Wikimedia Commons
Every computer has many software ports, or connection points for communications. Think of these as doors. Firewalls allow us to lock most of the doors and monitor who (what data traffic) comes in and goes out, blocking anything known to be dangerous.
(Recall that hardware ports are a way to "plug something into" your computer.)

A network firewall
By Bruno Pedrozo (Feito por mim) [GFDL or CC-BY-SA-3.0-2.5-2.0-1.0], via Wikimedia Commons
Malicious software and antivirus
Commonly, a computer user can be tricked or forced into downloading software onto a computer that is of malicious intent. Such programs are known as malware and come in many forms, such as viruses, Trojan horses, spyware, and worms. Malicious software is sometimes used to form botnets. (A botnet is a network of "zombie" computers that have been taken over by a "bot" that performs large-scale malicious acts for the creator of the botnet.)
Antivirus
We talked about antivirus software in an earlier module.
Antivirus programs and Internet security programs are useful in protecting a computer or programmable device from malware.
Such programs are used to detect and usually remove viruses; however, it is now common to see security suites, containing also firewalls, anti-spyware, theft protection, and so on, to more thoroughly protect users. While you may have two kinds of AV software, typically only one should be used for on-access scanning of files. Similarly, only one firewall should be used on a PC system. If you have two AV programs, and a firewall that came with your OS, you need to pick one and disable the others.
Traditionally, a user would pay for antivirus software; however, computer users now can, and do, download from a host of free security applications on the Internet.
Your router may also have a firewall protecting the network. This can make it a bit more difficult to specify that a particular application (or kind of network traffic) is allowed, since it has to get through both firewalls. Security comes at a cost, even if the software is free.
Always look first
Make sure that you research any software before you download it. The following are examples of malware that are only named to trick you: (links are to Wikipedia, not the software)
- Internet Security Essentials
- ANG Antivirus (knock-off of the legit AVG Anti-virus)
- MacSweeper
How DoS works
If a group of my friends and I repeatedly called your cell phone, as quickly and as often as possible, we would deny you (and your friends) the normal use of your phone. In the Internet, the attack usually comes as a concerted effort by a number of attacking hosts. The attack might be as simple as repeatedly requesting a web page or a file download.
See botnet.
Denial-of-service attack
A denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a computer resource unavailable to its intended users. Although the means to carry out, motives for, and targets of a DoS attack may vary, it generally consists of the concerted efforts of person or persons to prevent an Internet site or service from functioning efficiently or at all, temporarily or indefinitely.
502 Service Temporarily Overloaded - Server congestion; too many connections; high traffic. Keep trying until the page loads. 503 Service Unavailable - Server busy, site may have moved, or you lost your dial-up Internet connection.
Buffer overflow attacks
A buffer overflow is an attack that could be used by a hacker to get (sometimes full) system access by exploiting a vulnerability in software on the host. Most security applications and suites are incapable of adequate defense against these kinds of attacks.
The vulnerability (software flaw) is typically a combination of design, implementation and testing errors by the software engineers and programmers who developed the exploited system or application. Because of the lack of built-in protections, the programming languages C and C++ are often associated with buffer overflow errors.
Phishing
Phishing is a way of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites, auction sites, online payment processors or IT administrators are commonly used to lure the unsuspecting public. Phishing is typically carried out by e-mail spoofing or instant messaging, and it often directs users to enter details at a fake web site with a look and feel that are almost identical to the legitimate one. Phishing is an example of social engineering techniques used to deceive users, and exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical security measures.[src]
Note that unlike pharming, phishing tricks the user into actively selecting the fake web site. Users should look carefully at the link address (URL) when it pops up, but before clicking, comparing it to where they believe the link would take them. (A link anchor can say anything: free ice cream for life.) If an IP address, rather than a host domain name appears, assume it has bad intent. If you still believe it to be legitimate, go to the web site the way you normally would (type in the URL) and login – do not click their link. Any legitimate communication should be available to a logged in user.

What a typical "phishing" e-mail may look like. A real phishing attempt would claim to be from an actual bank the customer belongs to. Notice how it tries to establish authenticity by using the bank's logo and providing what appears to be a link to a web site the customer has been to many times before.
public domain image
Another (safe) redirection: http://www.sru.edu for you to try.
Pharming
Pharming is a hacker's attack aiming to redirect a web site's traffic to another, bogus web site. Pharming can be conducted either by changing the hosts file on a victim's computer or by exploitation of a vulnerability in (or "poisoning") the Domain Name Server. DNS servers are computers responsible for resolving Internet names into their real (IP) addresses. Unfortunately, there is no way for a user to know this has occurred unless the target doesn't look or feel right, or as expected. In this case, you need a different communication mechanism – telephone them and ask if they have changed their web site.
In recent years both pharming and phishing have been used to gather information for identity theft. Pharming has become of major concern to businesses hosting ecommerce and online banking web sites. Sophisticated measures known as anti-pharming are required to protect against this serious threat. Antivirus software and spyware removal software cannot protect against pharming.
Social Engineering
Social engineering is the art of manipulating people into performing actions or divulging confidential information, rather than by breaking in or using technical cracking techniques. While similar to a confidence trick or simple fraud, the term typically applies to trickery or deception for the purpose of information gathering, fraud, or computer system access; in most cases the attacker never comes face-to-face with the victim. In addition to criminal purposes, social engineering has also been employed by debt collectors, skiptracers, private investigators, bounty hunters and tabloid journalists.[src]
Who are the cyber villains [src]
Hacker
The original term "hacker" originated in the 1960's, meaning a computer programmer who wants to learn the different programming languages & computer systems and, generally, to make them "better". That is, modify the system in ways intended to, somehow, improve or extend the services of the system. There was also a sense of not wanting to be "locked out". This description is based on the 1984 book "Hackers: Heroes of the Computer Revolution" by Steven Levy.
More recently, hackers are commonly thought of as being malicious. Hackers are also individuals who gain unauthorized access to computers and/or networks. There are often two types of hackers: Black-hat and White-hats, respectively referring to bad and good "guys" – the hacking community includes plenty of women.
Hackers generally participate in these activities to create challenges for themselves and usually there is no financial gain. Nevertheless, hacking is legally and ethically ambiguous. There are now ample opportunities in the open source community for white-hat hackers to learn and exercise their art.
Cracker
"Hacker" remains an ambiguous term because many reject the current media definition of all hackers being malicious. The term cracker was coined for hackers who break into computers and networks for corrupt purposes. (Unfortunately, the terms crack, cracker and cracking all have other meanings also.) Crackers typically seek financial or other monetary gains. Under this definition, a cracker is someone engaged in illegal activity. Examples include: pirating software, stealing people's credit card information, obtaining private information (for sale or ID theft), shutting down hardware, and altering or destroying data.
There are four different classes of crackers: Script kiddies, black-hat hackers, hacktivists, and cyberterrorists.
- Script kiddies are those that use the knowledge of others – directions they simply follow by rote – to attack systems.
- Black-hat hackers figure out how to attack systems. Their intentions range from unethical to illegal. The best are sometimes called "elites".
3. Hacktivists
"Hacker Activists" are people with a politically or socially motivated purpose who break into a computer system. For example, someone, who after breaking in, leaves a political or social viewpoint or opinion on the home page of a web site to express a position or practice they oppose. These hacktivists range from script-kiddies to black-hats and are distinguished by their intent.
Armed with what may become one of the most important weapons in the struggle for human rights – computer code – the "hactivists" are trying to give activists electronic ways to circumvent government surveillance and information management. Some (outside a particular government) may not consider this hacking at all, as activism does not, in itself, imply illegal or unethical activity.
Hacktivists have recently targeted a number of sites in response to what they view as the unfair treatment of PFC Bradley Manning and Wikileaks over the publication of US State Department messages.
I can't think of a better time to put in the following thought provoking sidebars.

Edward Snowden

WikiLeaks site
hacking 2016
4. Cyberterrorism
Cyber-terrorism is the leveraging of a target's computers and information technology, particularly via the Internet, to cause physical, real-world harm or severe disruption of infrastructure. As the Internet continues to expand, and computer systems continue to be assigned more responsibility while becoming more and more complex and interdependent, sabotage or terrorism via cyberspace may become a more serious threat. Individuals or groups can use the relative anonymity afforded by cyberspace to threaten citizens, specific groups (i.e. with membership based on ethnicity or belief), communities and entire countries, without the inherent threat of capture, injury, or death to the attacker that being physically present would bring. It could be defined as the use of information technology by terrorist groups and individuals to further their agenda. This can include use of information technology to organize and execute attacks against networks, computer systems and telecommunications infrastructures, or for exchanging information or making threats electronically.
Cyberterrorism can have a serious large-scale influence on significant numbers of people. It can weaken s country's economy greatly, thereby stripping it of its resources and making it more vulnerable to military attack. Cyberterror can also affect internet-based businesses. Like brick and mortar retailers and service providers, most web sites that produce income (whether by advertising, monetary exchange for goods or paid services) could stand to lose money in the event of downtime created by cyber criminals.
Safe Shopping
Shopping on the Internet is increasing dramatically. It could be likened to shopping at a very large flea market, except that this flea market includes almost all traditional, well-known vendors like Macy's, Sears and Amazon. Consider the following before purchasing:
- How well do you know the vendor?
- Unknown start-up vendors can be great, but fraud is rampant. Build a relationship with the vendor before making any large purchases – and watch your credit card statement closely. Consider using a well-known site that lets you buy from others, like Amazon.
- Do they use secure http?
- Never enter credit card (or personal) information if the site is not using HTTPS or if the site's "certificate" has expired or is otherwise flawed. The certificate is a hidden mechanism for assuring that a site is who they say they are. Even a well-known site may have been compromised.
- Credit cards only
- US law provides some safeguards for credit card transactions. What happens with a debit card is between you and your bank. The bad guys can empty your account (and more).
- Set up an online payment account
- Typically, you will need to give the service a credit card (or otherwise pay them), but then all transactions are handled through them. Generally, the service does some monitoring for unusual activity, adding a layer of "security".
 #163 Shop Safely Online
#163 Shop Safely Online
 #110 Browser Security: phishing
#110 Browser Security: phishing
 #142 Protect your identity
#142 Protect your identity







