


5.2. Software
System Software
Software is generally divided into two types: system software that keeps everything working, and application software that allows a user to accomplish some task (even if that task is playing solitaire). In this module, we will look primarily at system software. Application software and a third category, malware, will be discussed in following modules.
System software has the task of making your computer a usable system. All application programs work with the system software to accomplish their tasks. System software has three components: the operating system, system utilities (OS helpers), and drivers. As can be seen at right, the OS interacts with hardware through drivers.
Drivers
There is a plethora of computer hardware. For example, the number of disk drive models available, even from one manufacturer, can be surprisingly large. When you ask an application to "save" a file, it passes this request to the operating system. Rather than having the OS know how to accomplish this task with every possible disk drive, it instead knows how to do it for a generic (or virtual) drive. The manufacturer of the disk drive provides a (typically small) program to implement the functionality on their particular hardware, i.e., the small program is the virtual disk drive. That program is called a driver.
An analogy that you may find useful is that the driver acts as a language interpreter. All interactions pass through the driver.
It is key to note that, although the system you buy has many drivers pre-installed, those programs are provided by the device manufacturer. This is especially important if you are experiencing problems with a device or want to connect an unrecognized device. You will probably have to download a driver from the device manufacturer. That is, you might go to Western Digital for a disk driver, rather than Dell. (Some OEMs provide an easy way to do this, but they are really just redistributing software provided to them.)
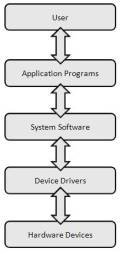
Simple Layered Interaction Model
By Paul Mullins: constructed

Language translation analogy for a driver
By Paul Mullins: constructed image

#22 Device Drivers
Operating System [src]
An operating system (OS) is software, that manages computer hardware resources, runs other programs, and provides common services for the user and application software.
For hardware functions such as input & output and memory allocation, the operating system acts as an intermediary between application programs and the computer hardware. Operating systems are found on any device that contains a computer – from cellular phones and video game consoles to supercomputers and web servers.
Examples of popular modern operating systems are: UNIX (Linux & Mac OS), Microsoft Windows and various mobile operating systems like Android and iOS.
Early computers were built to perform a series of single tasks, like a calculator. Operating systems did not exist in their modern and more complex forms until the early 1960s. When personal (home) computers by companies such as Apple Inc., Atari, IBM and Amiga became popular in the 1980s, vendors added operating system features, such as multi-user and multi-tasking functionality, that had previously become widely used on mainframe and minicomputers (that once bridged the gap between mainframes and PCs). Later, many features such as graphical user interfaces were developed specifically for personal computer operating systems.
An operating system consists of many parts. One of the most important components is the kernel, which controls low-level processes that the average user usually cannot see: it controls how memory is read and written, the order in which processes (running programs) are executed, how information is received and sent by devices like the monitor, keyboard and mouse, and decides how to interpret information received from networks. The user interface is a component that directly interacts with the computer user, allowing him or her to control and run programs. The user interface may be graphical with icons and a desktop, or textual, with a command line. Application programming interfaces provide services and code libraries that let applications developers write modular code.
Which features are considered part of the operating system is defined differently by some. For example, Microsoft Windows considers its user interface to be part of the operating system, as described above. On the other hand, Unix and Linux have a long history of allowing the end user to choose, or even to create their own, user interface.
For our purposes, the operating system always resides in RAM while the computer is operating.
Embedded Operating Systems
While the distinction is mostly import to technophiles, hand-held devices (including early smartphones) use(d) a class of operating system that is called "embedded". (List of embedded OSs.) Embedded systems, on the other hand, is a term generally used to refer to (usually real-time) systems with limited functionality. Embedded systems are quite common. They are in many devices, such as cars, microwave ovens, printers, etc. Embedded-OS devices are becoming much more common.
 How Operating Systems Work
How Operating Systems Work
 Taking a Slurp of Android Ice Cream Sandwich
Taking a Slurp of Android Ice Cream Sandwich
User Interface
From a user perspective, the user interface (typically a GUI) is the operating system. Actually this is just the way you, the user, can talk directly to the OS to accomplish system level tasks. As noted above, Microsoft considers the user interface to be a part of the OS, while some others, notably Linux, allow you to choose (and change) the interface. In the workplace, you typically will not have a choice because IT departments like to keep to one kind of system.
The video at right follows the progression of Microsoft desktop interfaces from DOS, a command line interface, to some guesses about Windows 7. (It was recorded before the release).

#69 Mac v. PC (v. Linux)

#156 What is Windows anyhow?
System Utilities [src]
Utility software is a kind of system software designed to help analyze, configure, optimize and maintain the computer. A single piece of utility software is usually called a utility or tool.
Utility software should be contrasted with application software, which allows users to do things like creating text documents, playing games, listening to music or surfing the web. Rather than providing these kinds of user-oriented or output-oriented functionality, utility software usually focuses on how the computer infrastructure (including the computer hardware, operating system, application software and data storage) operates. Due to this focus, some utilities are rather technical and targeted at people with an advanced level of computer knowledge. Others are commonly used by all users – a task manager is shown on the right.
Most utilities are highly specialized and designed to perform only a single task or a small range of tasks. However, there are also some utility suites that combine several features in one piece of software. Most major operating systems come with several pre-installed utilities. You may have to (find and) add utilities for your smartphone, though.
Although utilities are part of the system software, they are not part of the OS per se. They are loaded into memory as needed, either by the user or the OS.
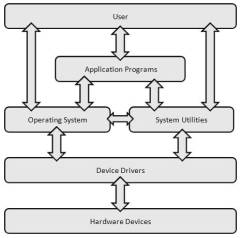
Enhanced Simple Layered Model
By Paul Mullins: constructed
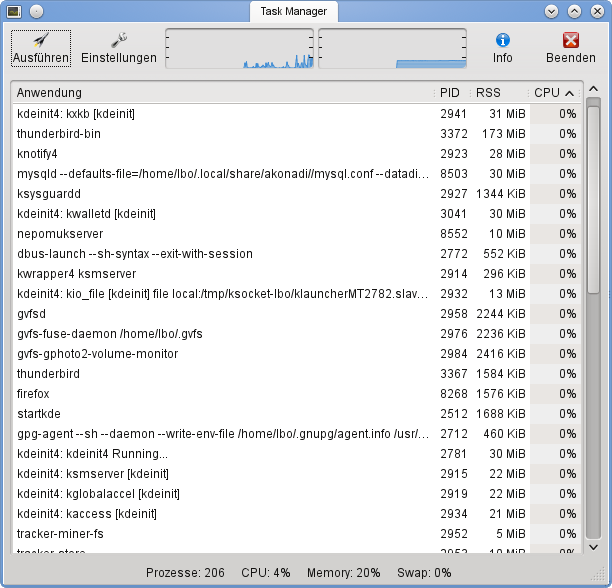
A Task Manager (process monitor)
By The xfce team
File Manager [src]
Files are containers for (binary) information saved on your hard disk. They may contain programs, or data saved by a program. That is, both your word processor – the app itself – and the various documents you have created exist as files. Files have names, like "writer.exe" and "report.doc", that are associated with the chunks of data that make up the file on the disk. Normally you run the word processor – causing the OS to copy it into RAM for execution – by either:
- selecting a shortcut on the desktop, or perhaps a "quick launch" tool bar,
- browsing to where the program (or a shortcut to it) is located and selecting it, or
- selecting a data file (report.doc) that is "associated with" the word processor.
The desktop icons exists as part of the file system. In a way, they just provide a nice looking and convenient way to do the same thing as browsing to the actual location and starting the program. That is, the first two methods are equivalent. When you select a data file to start the program, the OS uses the file extension (type) to consult a list of associations, maintained by the file manager. The associated application program is started and "given" the data file. The last step is more obvious when you ask to "open the file with" (right-click) and then select the program you want to use. (You may have noticed that when you install new software it sometimes changes the file associations.)
After starting the word processor, you either create a new document, or use the application's file browser (which talks to the OS file manager) to find and open your data file. Of course, if you selected a document to start the program, it will automatically open the selected document for you. Application actions like SAVE, SAVE AS, OPEN, and CLOSE all use the OS file manager to actually accomplish the task.
Beside making the point that both programs and documents (and even the OS itself) are stored in files, you can see that the application still uses the file manager as an intermediary. Copying a file is an action most efficiently performed by the file manager, not by starting an application, reading the data in and then saving it somewhere else. (See required sidebar below for more.)
Back to the file manager

Often you want to work directly with the files and that is where you use the system's file manager. You use this utility so often that there is a "must read" sidebar on the topic.
A file manager or file browser is a computer program that provides a user interface to work with file systems. The most common operations performed on files or groups of files are: create, open, edit, view, print, play, rename, move, copy, delete, and search/find, along with provisions for modifying attributes, properties and permissions (including sharing). Files are typically organized and displayed in a hierarchy.
Some file managers provide network connectivity. This is achieved by allowing the user to browse a connected file server and accessing the server's file system like a local file system — mounting a network drive. At SRU, the H: and I: drives are network drives that "follow you" around campus. These file, which are actually on a file server, are mounted across the network and appear to you to be on the PC you are using. (You can also access these drives from home, using sruwebaccess.sru.edu.)
-
SRU-Web-Access and the I (classworks) drive
A number of SRU faculty still use this rather dated method of sharing files... because it's much easier than using D2L. However students often report problems. In my experience the problem is either logging in
use: \srunet\email-id or accessing the files themselves. The problem here is that they apear to be on your computer, but they are actually on a read-only network file server. When you double-click a Word document, the application tries to write a temporary file to the directory. That operation will fail and you will be asked to enter a password. Since you don't have that permission, that will aslo fail.
Solution — just copy the file to your desktop before opening it.
What is your full name?
The fullname of a file includes its path and extension (type). Normally, the file manager keeps track of the path for you, and often displays the type as an icon. Following are three examples:
\Logfile.txt \Payroll\Timecards.xlsx \Payroll\Salaries\Leads.docx
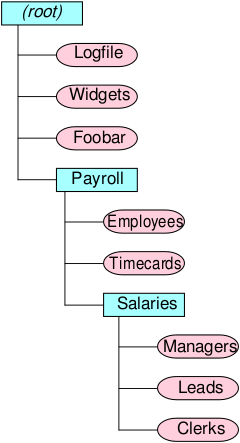
A file hierarchy
By http://en.wikipedia.org/wiki/User:TotoBaggins (http://en.wikipedia.org/wiki/File:FileFolders.svg) [CC-BY-SA-3.0], via Wikimedia Commons
Windows Explorer
Uploaded by Techmdrn. Fair use.
Mac Finder
Uploaded by Aido2002. Fair use.
A linux file manager
By Gürkan Sengün (Own work) [GPL, Public domain, GFDL or CC-BY-SA-3.0], via Wikimedia Commons
 #120 Undelete Files
#120 Undelete Files
 #79 Deleting Software without uninstall option
#79 Deleting Software without uninstall option
 #9 Sharing files on a home network
#9 Sharing files on a home network
Check Disk [src]
File systems are complex enough that they sometimes end up in disarray, usually because of a power outage, buggy software, or inappropriate action by the user (like taking a flash drive out before ejecting it).
CHKDSK (CHecK DiSK) is a command on computers running DOS, OS/2 and Microsoft Windows operating systems that displays the file system integrity status of hard disks and floppy disk and can fix logical file system errors. It is similar to the fsck command in Unix and the Disk Utility in Mac OS. Scandisk is available on Windows as a "tool" that can be accessed by right-clicking the root folder of the drive and selecting "Properties".

As it is relatively fast, you should check your file system fairly regularly and always before defragmenting the drive. Don't forget to scan removable, including flash, drives. These are more likely to need repair than the hard drive. The sidebar discusses what to do when failures occur.
Mac Disk Utility
Uploaded by Aanhorn. Fair use.

#74 Mac Disk Utility
Defragmentation [src]
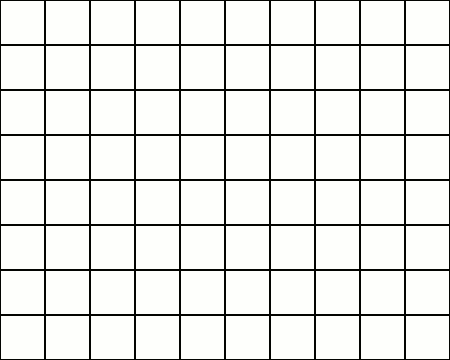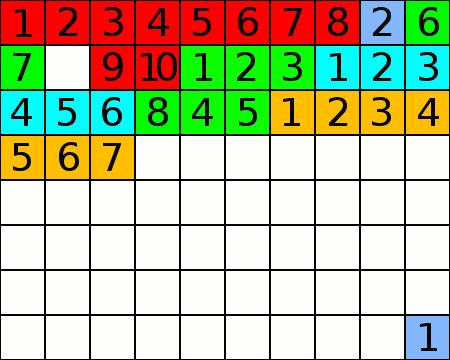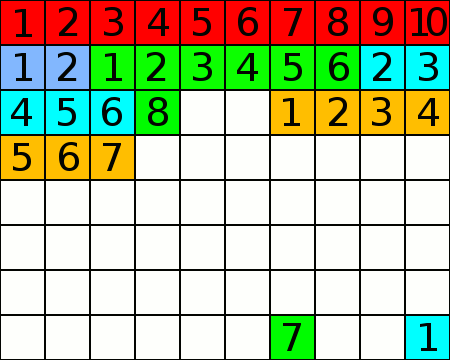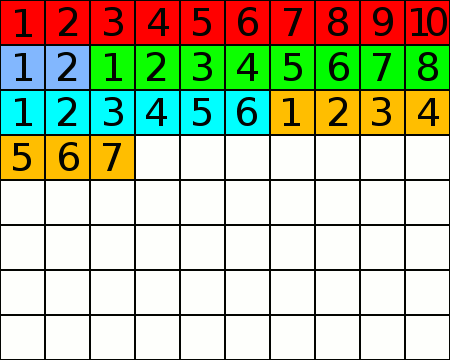
Fragmentation is the inability of a file system to lay out related data sequentially (contiguously) on the physical drive. In the image at right, a file was saved as three clusters (contiguous groups of segments).
Defragmentation is a process that reduces the amount of fragmentation in file systems. It does this by physically organizing the contents of the mass storage device to store files in a contiguous region if possible, or in the smallest possible number of regions (fragments) if not. It also attempts to create larger regions of free space to impede the return of fragmentation. Some defragmenters also try to keep smaller files within a single directory together, as they are often accessed in sequence.
Defragmentation is advantageous and relevant to file systems on electromechanical disk drives, i.e., traditional HDDs. The mechanical movement of the hard drive's read/write heads over different areas of the disk when accessing fragmented files is slower, compared to accessing the entire contents of a non-fragmented file sequentially without moving the read/write heads to seek other fragments. (Recall that access time is what make the disk slow relative to RAM – a fragmented file means multiple accesses.) Fragmentation is not a problem for flash (SSD) drives, as there are no moving parts.
Defragmentation is rarely effective until you have filled a substantial portion of the disk drive. Then, as it is a lengthy process, you might defrag the disk every few months. Always check for disk errors before defraging. Although it should never harm the file system, a backup and system restore point might be a good idea as well.
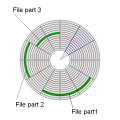
File fragmented into 3 clusters
By Paul Mullins: modified public domain image
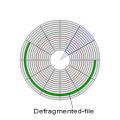
File defragmented into 1 cluster
By Paul Mullins: modified public domain image
Disk Defragmentation animation
By XZise (Own work) [GFDL or CC-BY-SA-3.0-2.5-2.0-1.0], via Wikimedia Commons
Backup [src]
Backups have two distinct purposes. The primary purpose is to recover data as a reaction to data loss, be it by data deletion or corrupted data (or a virus or hacking). Data loss is a very common experience of computer users. (67% of internet users have suffered serious data loss.) The secondary purpose of backups is to recover data from a historical period of time within the constraints of a user-defined data retention policy, i.e., getting a copy of the file you deleted or modified last year.
Backups should be done regularly. Ideally, the backup media will not be stored in the same location as the computer, avoiding having both destroyed by the same fire (for example). We will revisit this in a bit.
Backups are generally for user files and will not restore a complete working system.

#73 Backups 101
Restore Points [src]
In Windows System Restore, the user may create a new restore point manually, roll back to an existing restore point, or change the System Restore configuration. Moreover, the restore itself can be undone. Old restore points are discarded in order to keep the volume's usage within the specified amount. For many users, this can provide restore points covering the past several weeks. (Users concerned with performance or space usage may opt to disable System Restore entirely – not recommended.) Files stored on volumes not monitored by System Restore are never backed up or restored.
System Restore backs up system files of certain extensions (.EXE, .DLL, etc.) and saves them for later recovery and use. It also backs up the registry, most drivers and the user profile. Other user files need to be backed up independently. Restore points are created automatically under certain conditions.
Time Machine provides similar functionality for Mac OS X (10.5 Leopard).

#35 Registry 101: regedit, tools & System Restore
System Monitor [src]
A system monitor displays various statistics about system performance and allows tasks, such as:
- Quitting or "killing" a computer application – This is used commonly to stop a "hung" or frozen process. Also, see the sidebar on for misbehaving web pages.
- Viewing the computer's CPU load – a consistently high CPU load probably means it is time to get rid of all those programs you have running or even to replace your system.
- Checking the amount of Random Access Memory in use or swapped out – lots of swapping may mean you need to upgrade (increase) RAM
- Checking the capacity of storage devices (available as a property of the disk in Windows) – Over 50%, you should occasionally defrag the disk. Over 80%, you probably need to replace or add a drive.
- Monitoring the computer's network usage – for the average user this will tell you little, unless you aren't using the network. Lots of unexplained activity may mean you have malware on your machine or even an uninvited user (hacker).
- Inspecting running computer processes – You may have to use this to kill processes (malware) that do not show up as user applications. This can be effective in finding malware, if you keep a list of what is running on your system when you first receive it and update the list after each software install. Processes not on the list are suspect.

For Windows use the Task Manager and for Mac OS use the Activity Monitor. Linux has several tools available.
The sidebar includes use of the system monitor to kill processes.

System resource usage showing
CPU history
Memory & swap history
Network history
By 94thomas (Own work) [CC-BY-SA-3.0 or GFDL], via Wikimedia Commons
Activity Monitor
Uploaded by Fuzzy510. Fair use.
Network Utilities [src]
Network utilities are small software utilities designed to analyze and configure various aspects of computer networks. The majority of them originated on Unix systems, i.e., they are "power tools". The most common tools (found on most operating systems) include:
- ping is used to check connectivity to a host. It reports packet loss and latency (round trip time).
- traceroute (or tracert) shows the series of successive systems a packet goes through en route to its destination on a network, i.e., it traces the route the packets take.
- nslookup is used to query a DNS server for the IP address associated with a host domain name. This is like looking up a phone number by name in your contact list. (On Unix systems, the tools called “host” and "dig" are now preferred.)
Your primary use of these would be to ensure that your network connection is working. If the web browser is working, then these will be of little benefit to you. Problems will be more easily solved by contacting your ISP.
On most systems, these are entered as text commands using a command window (shell). Example usage for a Google web server:
ping www.google.com tracert www.google.com nslookup www.google.com
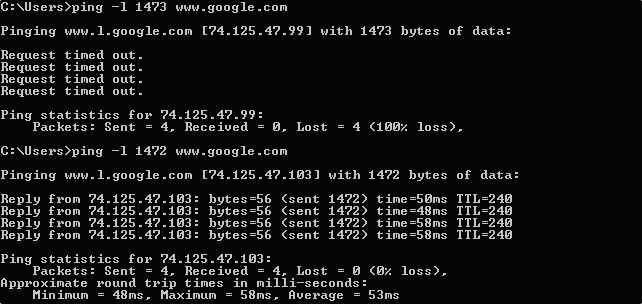
Sample ping results
By Thingg?? (Own work) [Public domain], via Wikimedia Commons
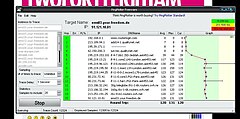
Sample traceroute
By Kuwaiti-Man (Own work) [Public domain], via Wikimedia Commons

#89 Trouble shooting an ailing network
Anti-Malware
This includes firewalls, anti-virus, intrusion detection, anti-spyware and adware. We will return to this topic in the module on malware.
Platform [src]
A computer platform is the combination of hardware and operating system. This is important to software development (and purchase), because software developed for one platform generally does not run on another. More technically, a computing platform includes some sort of hardware architecture and a software framework (including application frameworks). The combination allows software to run. Typical platforms include a computer's architecture, operating system, programming languages and related user interface (run-time system libraries or graphical user interface).
Multi-Boot
Dual boot, or more generally multi-boot, refers to the installation of multiple operating systems on the same computer (hardware). For example, a Windows PC might also have Linux on it or a Mac PC might have Linux and/or Windows on it.
Dual booting is accomplished by installing the operating systems on different disk partitions. A boot manager program then allows the user to select which of the operating systems to boot up. Getting to the boot manager may require a keystroke to interrupt the normal boot process. There are a number of boot loader programs available for Windows PCs. The Mac uses BootCamp.
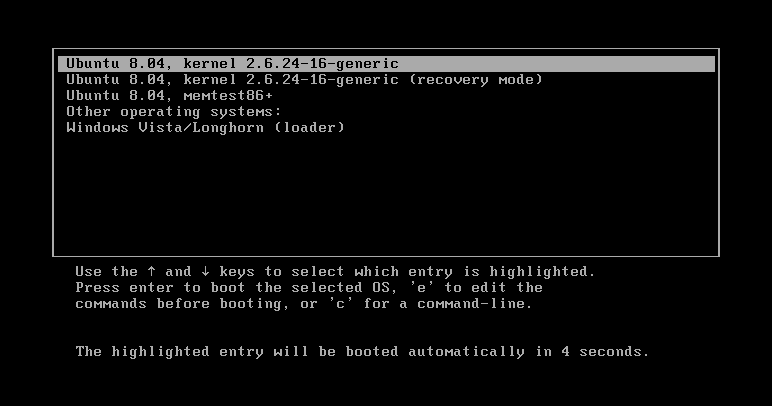
GRUB, with entries for ubuntu and for Windows Vista
public domain image
Virtualization
In the workplace, you may not have the option of dual booting your computer. Virtualization refers to emulating another platform on a running system, for example, using Mac Parallels to run Windows on the Mac desktop.
Virtualization is often used (installed by IT) on servers and mainframes to share resources.
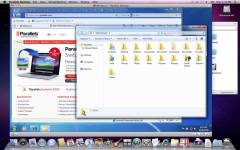
Parallels Desktop
Uploaded by Aanhorn. Fair use.
 #63 Windows on a Mac
#63 Windows on a Mac
 #217 Windows 7 on a Mac
#217 Windows 7 on a Mac
 #36 BIOS Basics
#36 BIOS Basics
 #38 Flashing BIOS
#38 Flashing BIOS
 #55 Intro Linux
#55 Intro Linux







